Prevent Phishing With The SLAM Technique

Phishing has become the top method cyber criminals use to attack companies, whether that’s hitting them with ransomware, breaching their databases, stealing their credentials and more. It is one of the biggest cyber security threats to companies, so it’s crucial they learn methods of phishing detection.
What is Phishing?
Phishing is a social engineering tactic that starts with an email. Social engineering is an attempt to trick the target (you or your employees) into sharing data, providing access to a system, or taking another action that the scammer can use for illicit gain. Phishing usually starts with an email (email phishing), but it can also involve text messages (smishing) and voice calls or voicemail (vishing). Spear phishing is targeted to a specific group while whaling targets an executive (CEO, CFO, CTO, etc.). These are all phishing.
You would think after decades of phishing attacks, companies would have figured out ways to get rid of them completely. But scammers constantly upgrade and evolve their tactics, which is why phishing continues to work. Companies must keep up their defenses as well.
Phishing Prevention Training
Phishing success depends on tricking an individual into taking an action. It just takes one moment of weakness to be deceived by a seemingly harmless email, one click on a file or links, and Pandora’s box is opened, giving the scammers access to your business.
That’s why prevention needs to start with your team — everyone from the summer intern to the CEO. Phishing training is easy to roll out, but ongoing reinforcement has to take place to keep phishing prevention top of mind. Studies have shown that employees will begin to forget what they learned and their skills will decrease just six months after their phishing detection training. You need to introduce your employees to a method they will understand and keep fresh in their memory. That is where the SLAM method for phishing identification comes in.
What Is the SLAM Method for Phishing Prevention?
SLAM is an acronym that can help people remember important information about phishing. The letters pertain to the four key areas of an email that must be checked in order to trust it.
SLAM stands for:
S = Sender
L = Links
A = Attachments
M = Message Text
Using the acronym will make checking emails quicker while still being thorough enough to be safe. It will help people avoid missing something that may lead them to accidentally expose their or their company’s information.
Check the Sender (S)
Checking the sender’s email is the first step in the SLAM method. Scammers will likely use a look-alike address or spoof a legit company address to trick people into trusting the email.
One common tactic is to include a real company's address inside their fake one. For example, the sender's email might be @emcom.bankofamerica.com, where the scammer is pretending to be from Bank of America, using the real company’s URL in a new domain to trick you.

You can quickly determine whether the email is a scam by searching the address used. You’ll likely find warnings that tell you it is a phishing email.
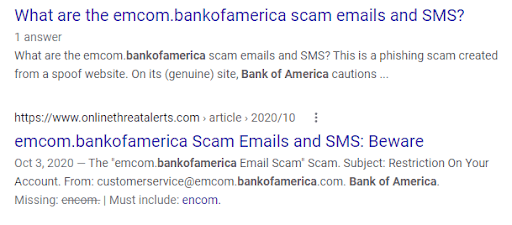
In a spoofed email, the sender’s email looks accurate, but it’s masking another with some code. You can look at the email source code to be sure (how to do this varies by email provider) or contact the person or business the email is supposed to be from to verify they sent it.
This last prevention tip is why spoofing executive emails is so common. Who wants to call up their CEO to ask, “Did you really send an email asking me to buy Target gift cards?” Make sure your company culture has a plan for this type of communication.
Hover Over Links (L) Before Clicking
A popular way scammers get their target's information is with the use of hyperlinks. Many people believe their anti-virus filters will protect them from clicking these links, but they do not. Anti-virus software can filter any attachments that may contain malware, but in the case of a hyperlink, the actual link is not unsafe. What’s unsafe is the site it takes you to if you click on it.
These links can come in many different forms: text links, images or buttons within the email. Before clicking on a link, you need to hover over it to see the URL. Noticing a sketchy URL will immediately tell you that the email is a scam.
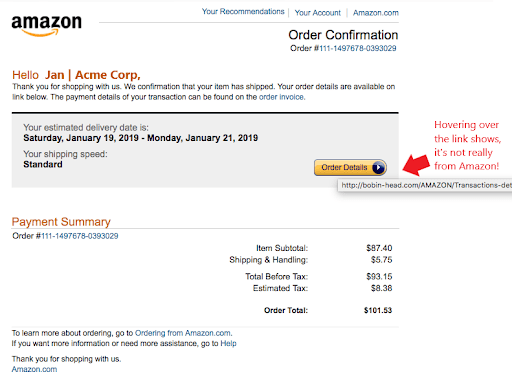
If you are using a touch screen or handheld device, it can be tricky to check the URL without accidentally clicking on it. In this case, it is best to just ignore the links and use other methods to detect whether or not the email is a scam.
Be Wary of Email Attachments (A)
You used to be able to tell if an attachment was OK based on the type of file it was. Not anymore. Criminals can now infect all types of files with malware, including PDFs,and who wouldn’t quickly click a file labeled as a sales order or invoice? File attachments are widely used in phishing emails simply because they work.
Never open an unexpected or strange file attachment. Actually, never open any attachment without first scanning it with an anti-virus/anti-malware application.
Carefully Read the Message (M)
We all do it — scan through messages without reading them fully. Especially in the work environment, where we have hundreds of things to process. Though efficient, this can be unsafe if you come across a phishing email.
When scanning the email, you will likely miss small spelling or grammatical errors that can indicate it’s a scam. Even reading through the email, these errors can be difficult to spot, because our brains can automatically process words even if they’re incorrect. That is why it’s important to be thorough in order to catch any potential red flags in the email.
If you don’t have time to read the email carefully, don’t take any actions (clicking a link or downloading an attachment) until you can.
Get Expert Help With Your Phishing Prevention
Cyber criminals are smart and know how to trick you. Now that you’re aware of the dangers and you’ve learned the basics, you don’t have to manage the threat alone. We are here to help train and protect you and your employees. Contact us or book a meeting so we can help keep your company safe from phishing.
Share this Blog

Is Your Name or Birthday a Part of Your Password?
If so, you’re a part of the 59 percent of people who don’t follow proper password hygiene. More than 70 percent of passwords are used for more than one system, meaning if cybercriminals crack one, they can access a lot more accounts.
Our free Enterprise Password Management Guide will give you the best password hygiene practices to help you secure your computer and your business.
Download the Guide
Explore the Latest Trends in IT

AI Guiding Principles

Edge vs Chrome Security: Which Is the Best Browser for Your Business?

Unlocking Security: The Power of Password Managers and Passkeys for Business Professionals




