Multi Factor Authentication: What the Microsoft MFA Warning Really Means

Multi-Factor Authentication (MFA) Options
Multi-factor authentication simply means that to log in to your account you need at least two factors: something you know (like a password) and something you possess (like your smartphone). When you use your credit card at a retail store or at a gas station and you are required to enter your zip code, that’s an example of two-factor authentication (2FA). The zip code is something you know and the credit card is something you have.
Securing your account with only a password is one-factor authentication, which puts you at greater risk, even when you use a strong, unique password. MFA generally requires that you enter a one-time password (OTP) that changes on a preset frequency in addition to your password to log in. With MFA enforced, hackers and cyber criminals can steal or guess your passwords but will be blocked from accessing your accounts unless they can supply the correct OTP within the time limit .
There are several different ways that the OTP can be delivered to you during a login and many if not most sites provide the option to choose the method that works best for you. Those methods typically include OTPs sent via text or voice call or an OTP access through an authenticator app such as Authy. More on that in a bit.
The Microsoft MFA warning encourages people not to rely on text (SMS) or voice calls for OTPs because of security weaknesses in the phone system. Rather, users should use more secure methods such as an authenticator app whenever possible.
Text, Call or Email Based OTPs
One option is to have the OTP sent to your phone via text (SMS) message when you log in. The main problem with this method is that cyber criminals can steal your phone number and receive your texts with a method called SIM jacking. And they never need contact with you or your phone to do it. All they have to do is convince one person who works for your mobile carrier that they are you and ask to transfer your SIM to a new phone. Learn more about SIM jacking.
Another option is to receive a phone call that prompts you to allow the login. In some cases, an inattentive user may be fooled to allow a hacker to log in.
These two methods are typically the easiest to use because there is no special hardware or software required and most people already know how to use text.
Microsoft called out both of these methods as far less secure than using an authenticator app. Not only for the reasons above, but also because the public phone networks are unencrypted and can be compromised with commonly available tools and know-how.
Email based OTPs have the same issues.
Thankfully voice call and email based OTPs are rarely offered anymore, and if they are an option, you should steer clear of them and look for the more secure options we cover next.
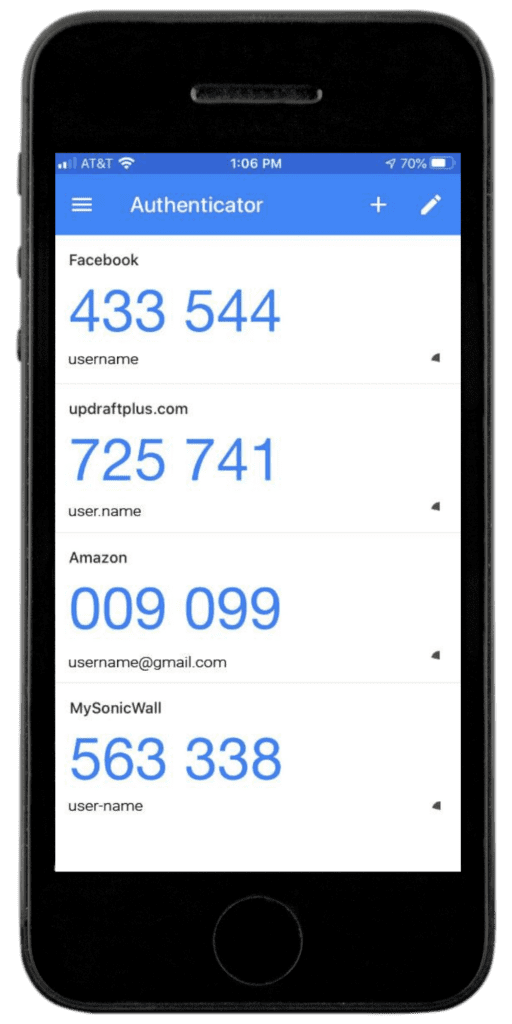
Authenticator Apps
Authenticator apps are software designed to sync with a site and generate OTPs to log in to that site. See the screenshot above that shows OTPs for various different sites. Typically you will install the authenticator app on your phone and then scan a QR code for a given site that links the app to that site. Then, when you attempt to log in, you will be required to enter the OTP from the authenticator app. The codes are different for each account and refresh every 30 seconds (see illustration).
Using the screen shot above as an example, if you were trying to log in to Amazon, you would enter your username and password (credentials) and then be prompted for the OTP. In this case, you would have 30 seconds to enter 725741. After 30 seconds, a new OTP will be generated.
Some sites will allow you to use an authenticator app in one of two ways: In the first way, you simply open the app and type in the OTP for a given site when prompted. In the second way, you receive a push notification from the app that asks you to approve the login and when you authorize it, typically by pressing a button on the screen, the app sends the OTP back to the site. While push notifications are more convenient, unless you’re paying careful attention when the push notification comes, you can be fooled into giving a hacker access. Additionally, you could press the button by accident (when’s the last time you completed an in-app purchase without meaning to?).
Microsoft has one the best authenticators available for both Android and IOS systems and there are others like Authy (mentioned above) that you can use. But note that not every authenticator app is supported by every site.
Authenticator apps are more secure than text based or voice call based OTPs because the data is encrypted AND, an attacker would need your phone and the synced authenticator app to access your account. If you are using a strong password to lock your phone (and you are, AREN’T YOU?) in conjunction with an authenticator app, it will be very difficult for an attacker to access your accounts.
“Better Than Nothing”
Unfortunately, not all websites and digital platforms support authenticator apps as an option for MFA. Warnings like the recent one from Microsoft are slowly helping to change that. As consumers become more aware of the risks and more comfortable with authenticator apps, companies will be more likely to include it as an option.
When possible, use an authenticator app and manually enter the OTP, which is more secure than push notifications sent to the app.
If that’s not an option, use the text option which is generally universally supported and easy to use. It’s less secure than an authenticator app, but far more secure than one-factor authentication.
Remember, any MFA is still better than having no MFA at all!
Bottomline for Multi-Factor Authentication (MFA)
- First and best choice: MFA app with manual entry of OTP
- Second choice: MFA with OTPs by push notifications
- Third choice: MFA with OTPs via text
If you don’t have a smartphone, aren’t allowed to carry a smartphone into secure areas where you need to log in, or want even better security than an authenticator app, you can use a hardware security key, like a Yubikey for the OTPs. These devices are generally about the size of a USB drive and plug into your device. Learn more about them here: https://www.zdnet.com/article/best-security-key/.
As a managed services provider, our IT support includes helping your business use multi-factor authentication to protect your accounts as well as training your team about its importance and how to use it. Looking for managed or enterprise IT support? Contact us or book a meeting for a quick, no pressure consultation (virtual or in person).
Share this Blog

Is Your Name or Birthday a Part of Your Password?
If so, you’re a part of the 59 percent of people who don’t follow proper password hygiene. More than 70 percent of passwords are used for more than one system, meaning if cybercriminals crack one, they can access a lot more accounts.
Our free Enterprise Password Management Guide will give you the best password hygiene practices to help you secure your computer and your business.
Download the Guide
Explore the Latest Trends in IT

Microsoft 365 and Google Workspace: The Importance of Backing Up Your Cloud-Based Applications

AI Guiding Principles

Edge vs Chrome Security: Which Is the Best Browser for Your Business?




